Manufacturers or developers typically set default credentials, such as username and password combinations, for devices, software, and systems. These credentials are intended for initial access. A threat actor may exploit default credentials to gain unauthorized access to the system or data.
Clone this current repo recursively
git clone --recursive https://github.com/qeeqbox/default-credentialRun the webapp using Python
python3 default-credential/vulnerable-web-app/webapp.pyOpen the webapp in your browser 127.0.0.1:5142
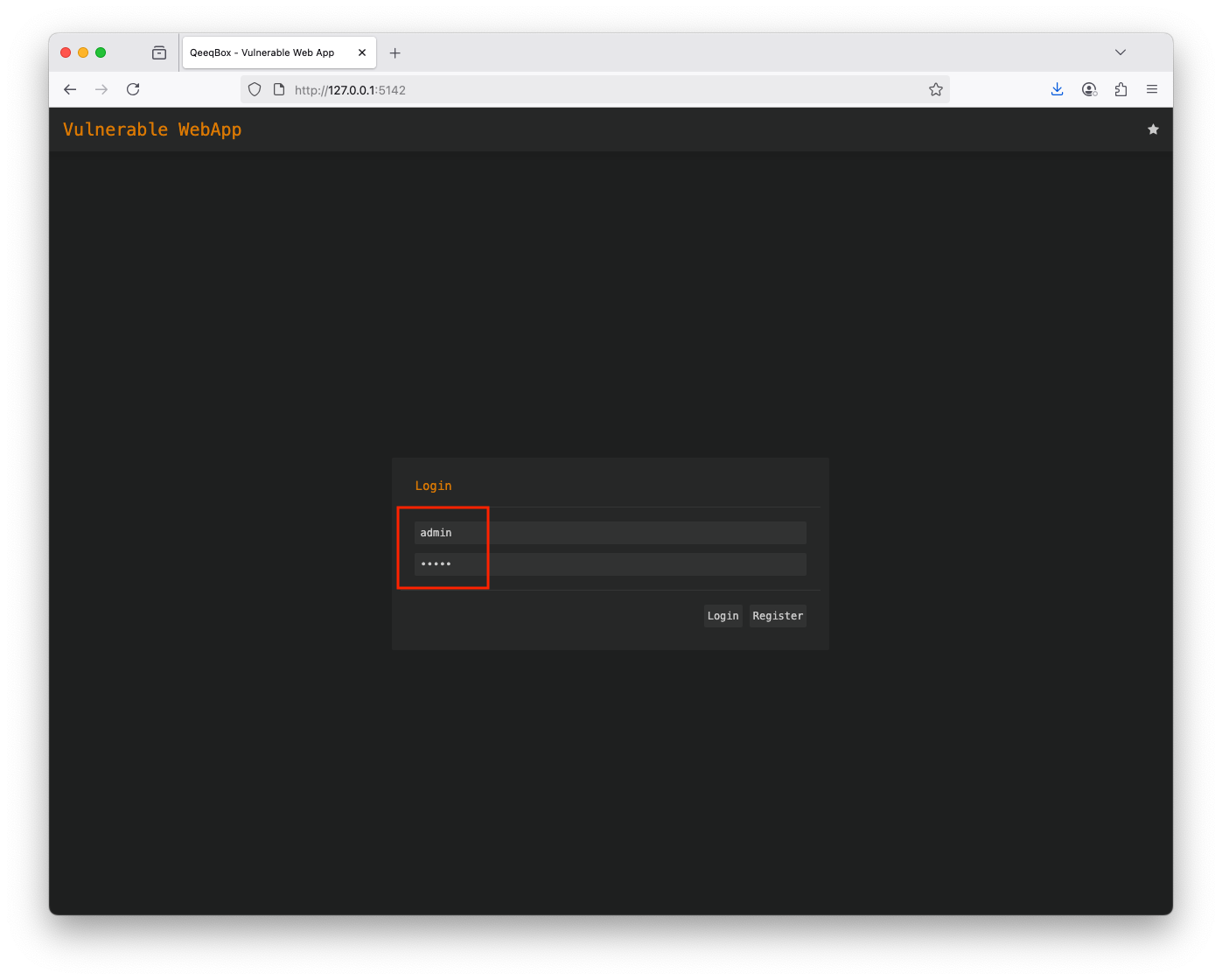
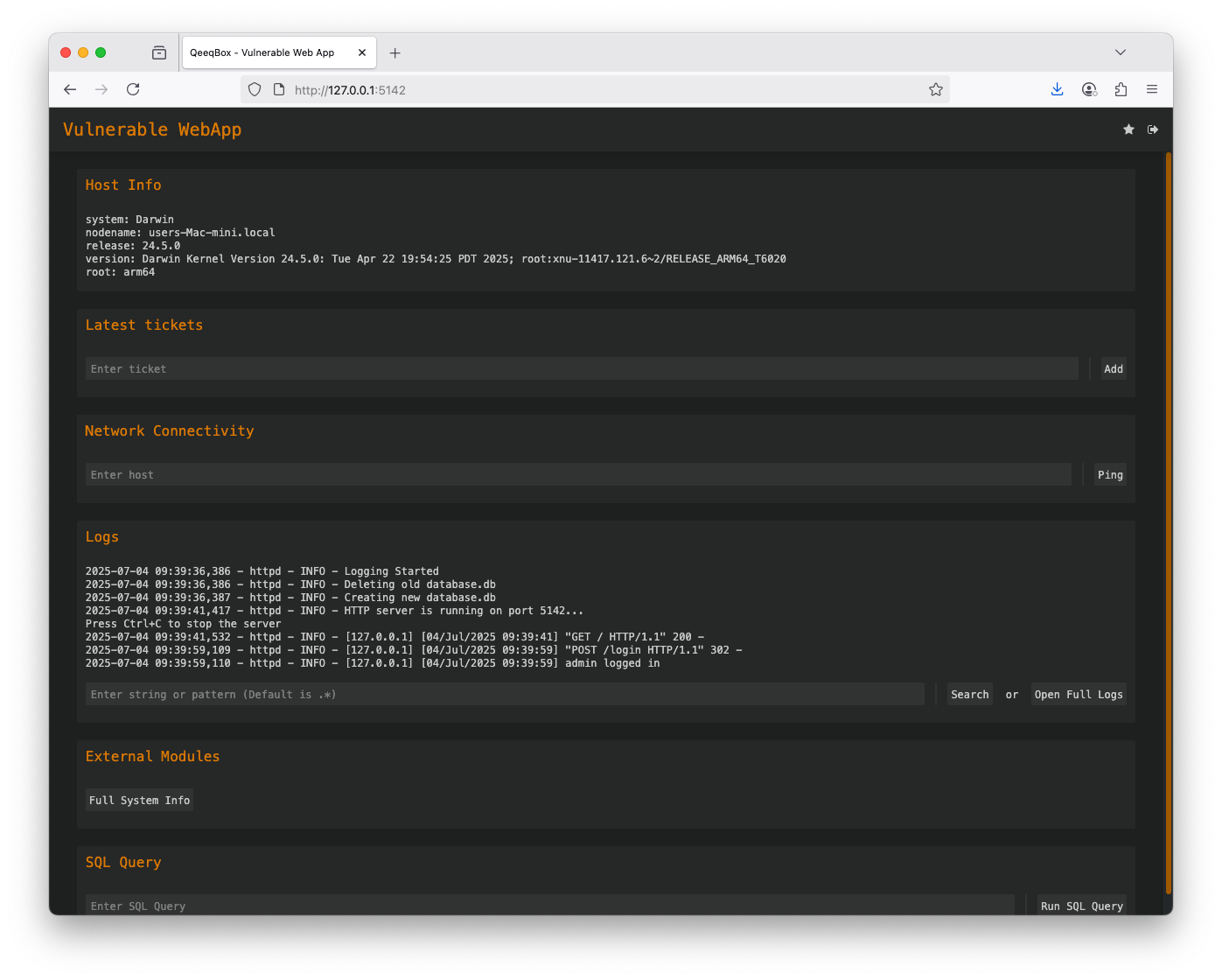
Use the default credentials (username: admin and password: admin) to login You have full control over the web app interface- Unauthorized Access
- System Compromise
- Operational Disruption
- Legal and Financial Damage
- Compliance Failures
- Reputation Damage
- Disable, remove or change default credentials
- Alternative Authentication Mechanisms
91f9b046-b802-425a-b71b-64c21c6b1c0f